The Data Breach That Exposed Millions
A fintech startup failed to secure its APIs, allowing attackers to steal sensitive user data.
The problem? Weak authentication, lack of encryption, and no rate limiting.
The solution? A robust security architecture, implementing OAuth, JWT, TLS, encryption, and firewalls to protect user data and prevent attacks.
Why Security Matters in System Design
Security ensures confidentiality, integrity, and availability of systems.
Example: A banking app must ensure transactions are secure, tamper-proof, and available 24/7.
Key Threats:
Data Breaches – Unauthorized access to user data.
DDoS Attacks – Overloading systems with excessive traffic.
Man-in-the-Middle Attacks – Intercepting unencrypted data.

Authentication & Authorization
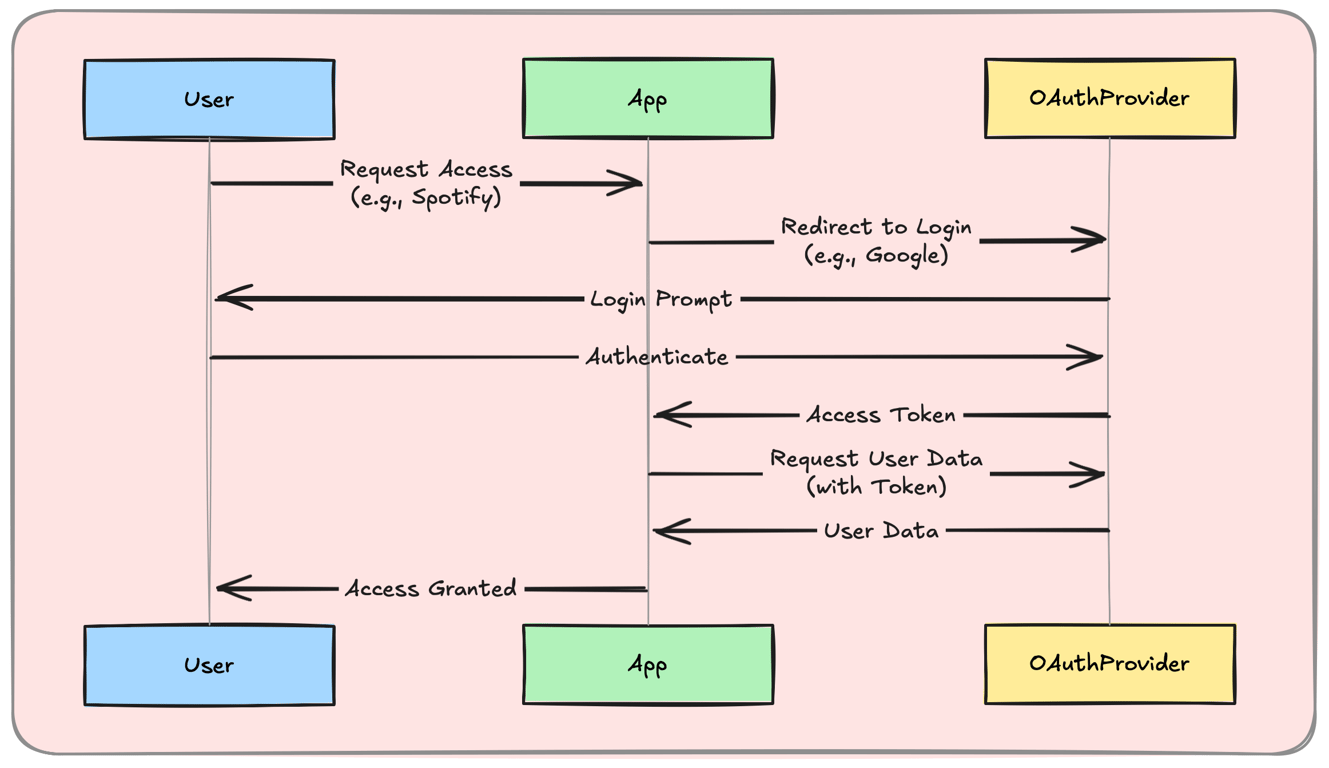
1. OAuth – Secure Third-Party Access
OAuth (Open Authorization) allows users to grant limited access to applications without sharing passwords.
How It Works:
User logs in via Google, Facebook, or GitHub.
OAuth provider issues an access token.
The app uses this token to access user data securely.
Example: Logging into Spotify using a Google account.
2. JWT – Secure Token-Based Authentication
JWT (JSON Web Token) is a compact, encrypted token used for secure API authentication.
Example: When a user logs in, the server returns a JWT, which is sent with each request to verify identity.
Key Features:
Stateless Authentication – No need to store sessions in a database.
Signed & Encrypted – Prevents tampering.
Example JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...Data Encryption – Protecting Sensitive Information
Encryption ensures that even if data is stolen, it remains unreadable.
Types of Encryption:
TLS (Transport Layer Security): Encrypts data in transit.
AES (Advanced Encryption Standard): Encrypts stored data.
Example: Websites with HTTPS use TLS encryption to protect user credentials.
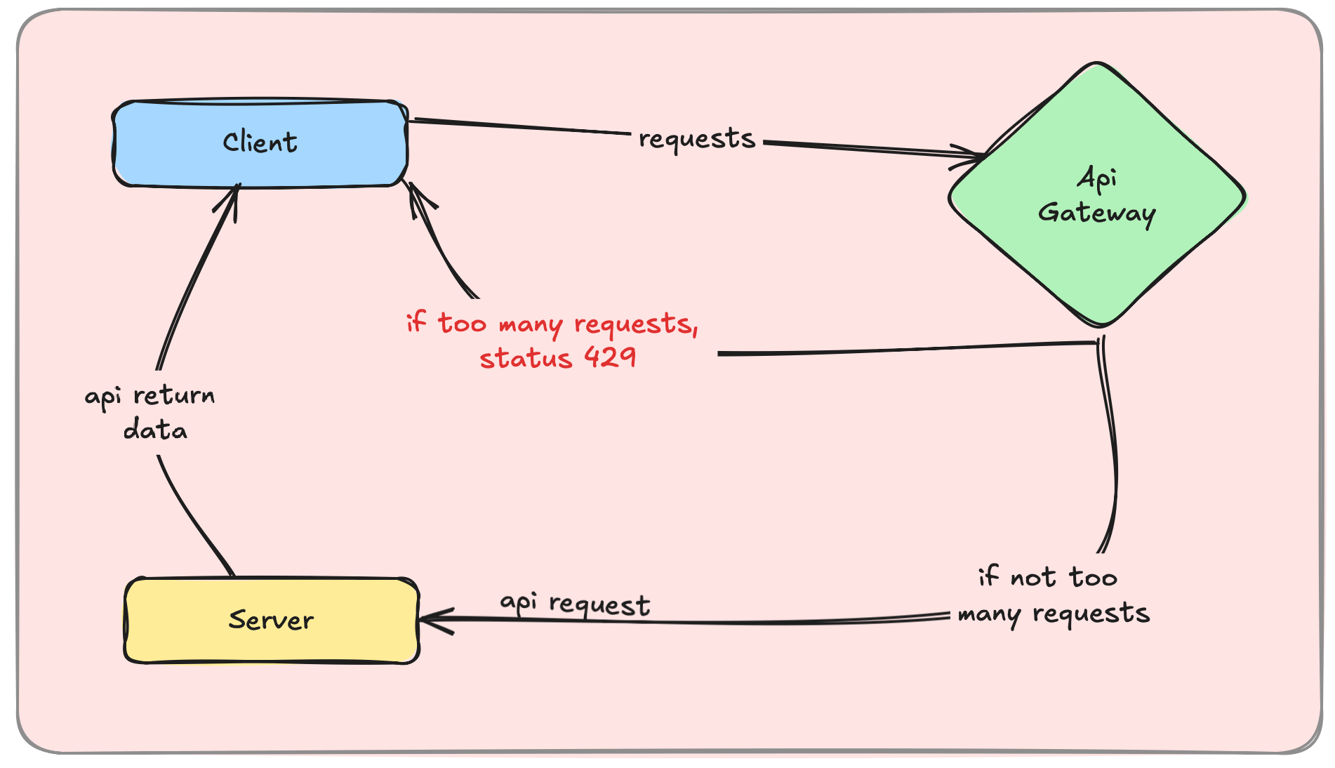
Rate Limiting – Preventing API Abuse
Rate limiting controls how many requests a user can send within a timeframe.
Key Benefits:
Prevents DDoS attacks by rejecting excessive requests.
Protects API performance by limiting load.
Example: An API allows only 100 requests per minute per user.
Firewalls – Blocking Unauthorized Access
Firewalls filter incoming and outgoing traffic to prevent cyberattacks.
Types of Firewalls:
Network Firewalls: Block traffic at the server level.
Web Application Firewalls (WAFs): Protect APIs from SQL injection and cross-site scripting.
Example: Cloudflare WAF blocks malicious API requests before reaching the server.
Real-World Use Cases
1. Banking & Financial Applications
OAuth secures third-party transactions.
JWT tokens authenticate banking API requests.
TLS encryption protects transaction data.
2. E-Commerce Platforms
Rate limiting prevents bot-driven checkout abuse.
WAF protects against SQL injection and API attacks.
3. Cloud-Based SaaS Applications
OAuth-based SSO (Single Sign-On) enhances user authentication.
Firewalls and intrusion detection prevent unauthorized access.
Conclusion
A secure system design protects users and prevents attacks.
OAuth & JWT handle authentication securely.
TLS & AES encryption protect data in transit and at rest.
Rate limiting & firewalls prevent abuse and unauthorized access.
Next, we’ll explore Data Consistency & Storage Strategies – ACID, BASE, Event Sourcing, CQRS.


